Migrate Secure Firewall ASA to Secure Firewall Threat Defense with the Firewall Migration Tool in Security Cloud Control
The Secure Firewall migration tool in Security Cloud Control lets you to migrate configurations from live ASA devices that are managed by Security Cloud Control or using a configuration file extracted from an ASA device. To read more about the Secure Firewall ASA configurations supported for migration, see ASA Configuration Support in the Migrating Cisco Secure Firewall ASA to Cisco Secure Firewall Threat Defense with the Migration Tool book.
Select Source Configuration
After launching your migration instance from Security Cloud Control, choose Cisco ASA in Select Source Configuration and click Start Migration. You can either manually upload an ASA configuration file or choose any one of the Security Cloud Control-managed ASA devices listed on the Connect to ASA pane. If you are trying to select a Security Cloud Control-managed device, note that devices having Configuration Status as Synced are only listed by the migration tool; if you do not see the device you want to migrate in the list, check if the device configuration changes are up-to-date and synced with Security Cloud Control. Note that one ASA device can be selected as the source device by more than one user at the same time and the confuguration extraction takes place seamlessly. If you have one or more security contexts configured on your ASA device, the migration tool allows you to choose which context you want to migrate; you can also merge all your contexts to a single instance and then migrate them. Refer Select the ASA Primary Security Context for more information.
The migration tool parses the device configuration and displays a summary containing the parsed configurations. Click Next.
Select Target
In the Select Target page, the cloud-delivered Firewall Management Center provisioned on your Security Cloud Control tenant is selected by default, and the Firewall Threat Defense devices managed by that management center are listed. You can choose the Firewall Threat Defense device you wish to migrate your ASA configuration to or choose to Proceed without FTD. Note that the threat defense devices listed are displayed either as In Use or Available based on whether the device is being used in another migration instance. However, you can perform an override by clicking Change Device Status, selecting the device from the In Use list, and clicking Continue, which will make the device available for being selected as the target.
Caution | Changing the device status from In Use to Available impacts the ongoing migration instance that is using the device already. We recommend that you exercise caution when doing this. |
Choosing Proceed without FTD pushes only NAT objects, ACLs, and port objects to the cloud-delivered Firewall Management Center. For more information about the commonly used ASA features and their equivalent threat defense features, see Cisco Secure Firewall ASA to Threat Defense Feature Mapping guide.
To perform the procedure with more detailed steps, continue to Obtain the ASA Configuration File in the Migrating Cisco Secure Firewall ASA to Threat Defense with the Migration Tool guide.
|
Workspace |
Steps |
|
|---|---|---|
|
|
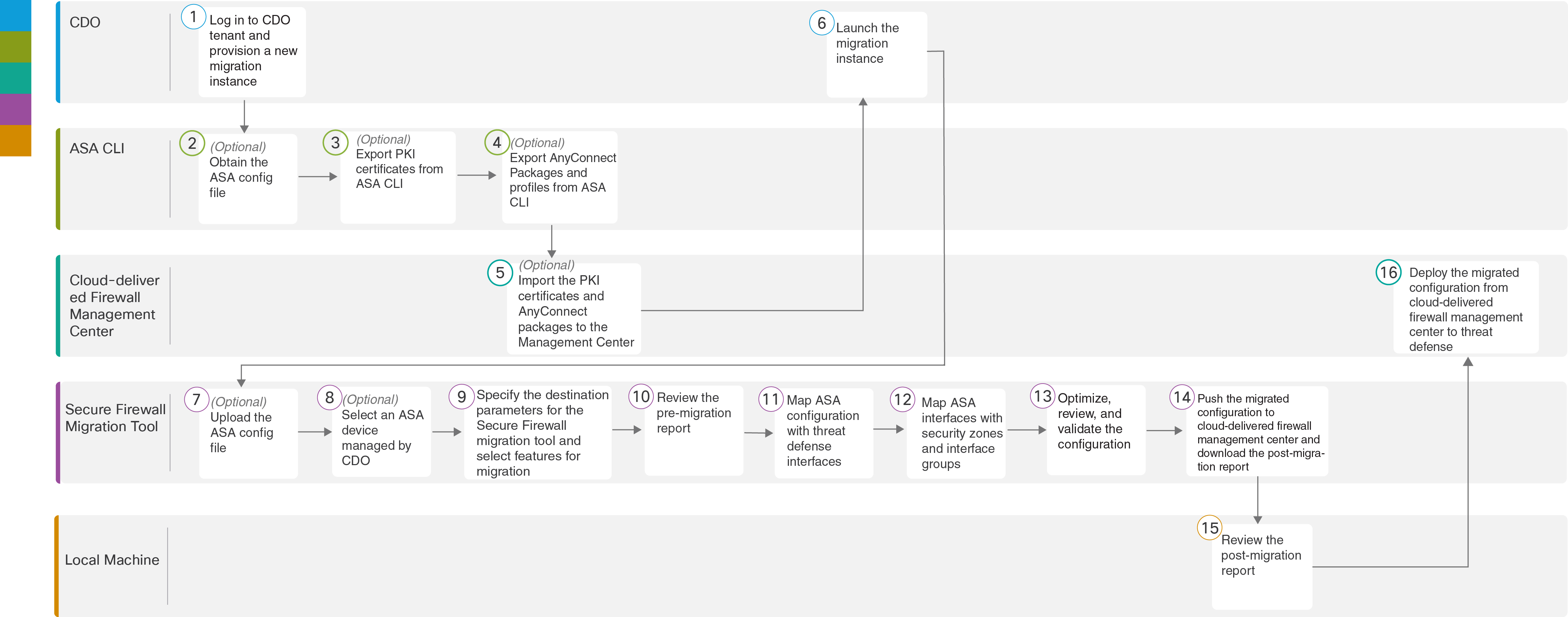
Security Cloud Control |
Log in to your Security Cloud Control tenant, navigate , and click the blue plus |
|
|
ASA CLI |
(Optional) Obtain the ASA configuration file: To obtain the ASA config file from ASA CLI, see Obtain the ASA Configuration File. If you intend to select a Security Cloud Control-managed ASA device in the Select Source Configuration, skip to Step 3. |
|
|
ASA CLI |
(Optional) Export public key infrastructure (PKI) certificates from ASA CLI: This step is required only if you are planning to migrate site-to site VPN and RAVPN configurations from ASA to threat defense. To export the PKI certificates from ASA CLI, see Export PKI Certificate from ASA and Import into Management Center. If you do not have remote-access VPN configurations on your device or you are not planning to migrate site-to-site VPN and remote-access VPN, skip to Step 7. |
|
|
ASA CLI |
(Optional) Export AnyConnect packages and profiles from ASA CLI: This step is required only if you are planning to migrate remote-access VPN features from ASA to threat defense. To export AnyConnect packages and profiles from ASA CLI, see Retrieve AnyConnect Packages and Profiles. |
|
|
Cloud-delivered Firewall Management Center |
(Optional) Import the PKI certificates and AnyConnect packages to the management center: To import the PKI certificates to management center, see Step 2 in Export PKI Certificate from ASA and Import into Management Center and Retrieve AnyConnect Packages and Profiles. |
|
|
Security Cloud Control |
Ensure that the status of the migration instance you created is Ready to Migrate and click Launch; the Secure Firewall Migration Tool opens in a new browser tab. |
|
Secure Firewall Migration Tool |
(Optional) Upload the ASA config file obtained from ASA CLI, see Upload the ASA Configuration File. If you are planning to migrate configuration from an ASA device managed by Security Cloud Control, skip to Step 8. |
|
|
|
Secure Firewall Migration Tool |
From the list of ASA devices shown, that are managed by your Security Cloud Control tenant, select the device whose configuration you want to migrate. If you have configured more than one security context on your ASA device, select the context you wish to migrate or choose to merge all the contexts to a singe instance in the Primary Context Selectiondrop-down. See Select the ASA Primary Security Context for more information. |
|
|
Secure Firewall Migration Tool |
On the Select Target page, the cloud-delivered Firewall Management Center provisioned on your Security Cloud Control tenant is selected by default. |
|
|
Secure Firewall Migration Tool |
Select a target device from the list of threat defense devices managed by your cloud-delivered Firewall Management Center or choose Proceed without FTD and proceed. |
|
|
Secure Firewall Migration Tool |
Download the pre-migration report and review it for a detailed summary of the parsed configuration. For detailed steps, see Review the Pre-Migration Report. |
|
|
Secure Firewall Migration Tool |
Map FTD Interface with the ASA configuration. Because the names of physical and port channel interfaces on your ASA and threat defense devices are not always the same, you can select to which interface in the target threat defense device you want an ASA interface to get mapped. For more information, see Map ASA Configurations with Secure Firewall Device Manager Threat Defense Interfaces. |
|
|
Secure Firewall Migration Tool |
Map ASA interfaces to existing threat defense security zones and interface groups. See Map ASA Interfaces to Security Zones and Interface Groups for detailed steps. |
|
|
Secure Firewall Migration Tool |
Optimize, Review and Validate Configuration with caution and ensure ACLs, objects, NAT, interfaces, routes, site-to-site VPN, and remote-access VPN rules are configured as intended for the destination threat defense device. See Optimize, Review and Validate the Configuration. |
|
|
Secure Firewall Migration Tool |
Once your configuration validation is a success, Push Configuration to the cloud-delivered Firewall Management Center. For more information, see Push the Migrated Configuration to Management Center. |
|
|
Local Machine |
Download the post-migration report and review it. To know more on what information the post-migration report contains, see Review the Post-Migration Report and Complete the Migration. |
|
|
Cloud-delivered Firewall Management Center |
Deploy the newly migrated configuration to the threat defense device. |
 button to start provisioning a new migration instance.
button to start provisioning a new migration instance.