Prerequisites for Adding an Active Directory Group to Security Cloud Control
Before adding an Active Directory group mapping to Security Cloud Control as a form of user management, you must have your Active Directory that is integrated with Security Cloud Sign On. If your Active Directory Identity Provider (IdP) is not already integrated, see identity provider integration guide to integrate a custom Active Directory IdP integration with the following information:
-
Your Security Cloud Control tenant name and region
-
Domain to define custom routing for (for example: @cisco.com, @myenterprise.com)
-
Certificate and federation metadata in the XML format
After your Active Directory integration is complete, add the following custom SAML claims in your Active Directory. The SAML claims and attributes are required, for you to be able to successfully sign-in to your Security Cloud Control tenant after your Active Directory integration is done. These values are case sensitive:
-
SamlADUserGroupIds - This attribute describes all group associations that a user has on Active Directory. For example, in Azure select + Add a group claim as seen in the screenshot below:
Custom Claims Defined in Active Directory 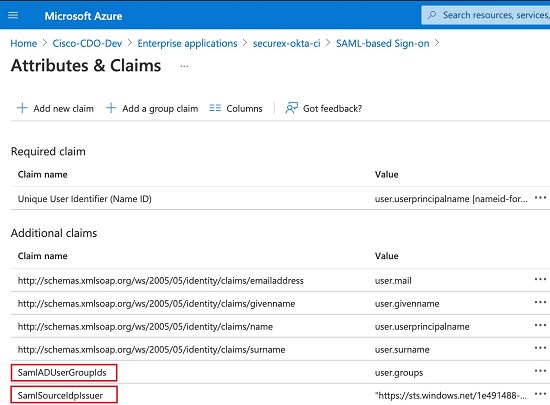
-
SamlSourceIdpIssuer - This attribute uniquely identifies an Active Directory instance. For example, in Azure select + Add a group claim and scroll to locate the Azure Active Directory Identifier as seen in the screenshot below:
Locate the Azure Active Directory Identifier 